Trust is good, quantum trickery is better
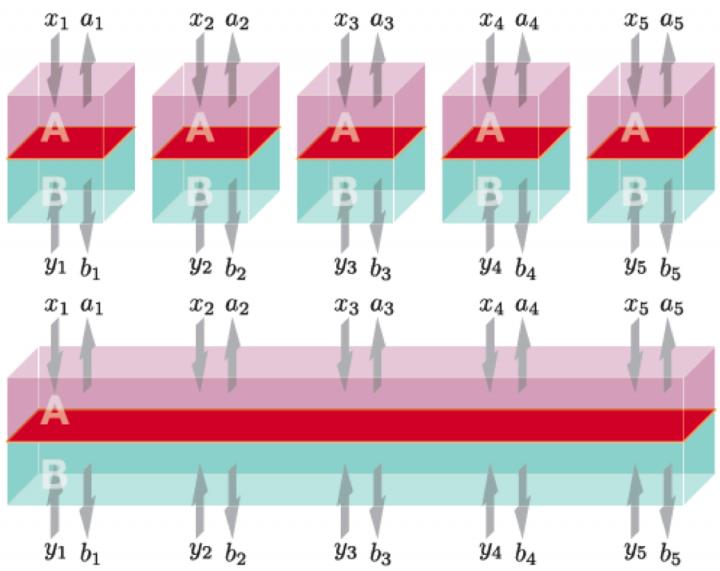
The key to proving the security of device-independent quantum cryptography in a regime that is attainable with state-of-the-art quantum technology is the realization that any attack strategy, no matter how complex (symbolized in the lower row), can be decomposed into a sequence of simple steps (upper row). (Image from Arnon-Friedman et al. Nature Comms 9, 459; 2018)
In quantum cryptography, the laws of quantum mechanics are exploited to send messages with higher security than is possible in conventional cryptographic schemes based on classical physical phenomena. In principle, quantum communication enables absolute security — that is, no adversary can intercept messages or tinker with them.
But in practice such unconditional security is not realizable. One main route for an unauthorized person to 'listen in' is to manipulate in advance the communication devices that will be used later.
Writing in Nature Communications, Rotem Arnon-Friedman and colleagues prove that there exist quantum-cryptographic protocols that ensure nearly optimal security even if the devices are manipulated, and that such device-independent quantum cryptography should be possible with current quantum technology.
Device-independent quantum cryptography is the 'gold standard' of quantum communication, as the advantages of quantum cryptography over its classical counterpart can be realized without having to worry whether the device used can be trusted or not. This is an appealing prospect, but so far device-independent quantum cryptography has been mostly a theoretical construct, with experimental requirements that are not achievable under realistic conditions.
Therefore the appeal of the new work of Arnon-Friedman, a PhD student in the group of Prof. Renato Renner in the Institute of Theoretical Physics at ETH Zurich, and co-workers in the US, France and the Czech Republic. The team developed a new theoretical concept, dubbed 'entropy accumulation', and applied it to quantum cryptography.
They find that any attack strategy, no matter how complex, can be decomposed into a sequence of simple steps. This is very helpful for security proofs, which are notoriously hard because every possible attack strategy that an adversary may conceive has to be taken into account.
With their new approach, Arnon-Friedman and her colleagues now prove, for the first time, the security of device-independent quantum cryptography in a regime that is attainable with state-of-the-art quantum technology, thus paving the way to practical realization of such schemes.
###
This work is a collaboration including scientists at ETH Zurich (Switzerland), the California Institute of Technology (US), École Normale Superieure de Lyon (France), Université de Lorraine (France) and Masaryk University (Czech Republic).
Media Contact
All latest news from the category: Physics and Astronomy
This area deals with the fundamental laws and building blocks of nature and how they interact, the properties and the behavior of matter, and research into space and time and their structures.
innovations-report provides in-depth reports and articles on subjects such as astrophysics, laser technologies, nuclear, quantum, particle and solid-state physics, nanotechnologies, planetary research and findings (Mars, Venus) and developments related to the Hubble Telescope.
Newest articles

A ‘language’ for ML models to predict nanopore properties
A large number of 2D materials like graphene can have nanopores – small holes formed by missing atoms through which foreign substances can pass. The properties of these nanopores dictate many…

Clinically validated, wearable ultrasound patch
… for continuous blood pressure monitoring. A team of researchers at the University of California San Diego has developed a new and improved wearable ultrasound patch for continuous and noninvasive…

A new puzzle piece for string theory research
Dr. Ksenia Fedosova from the Cluster of Excellence Mathematics Münster, along with an international research team, has proven a conjecture in string theory that physicists had proposed regarding certain equations….



