GhostTouch: Capturing cell phones contact-free
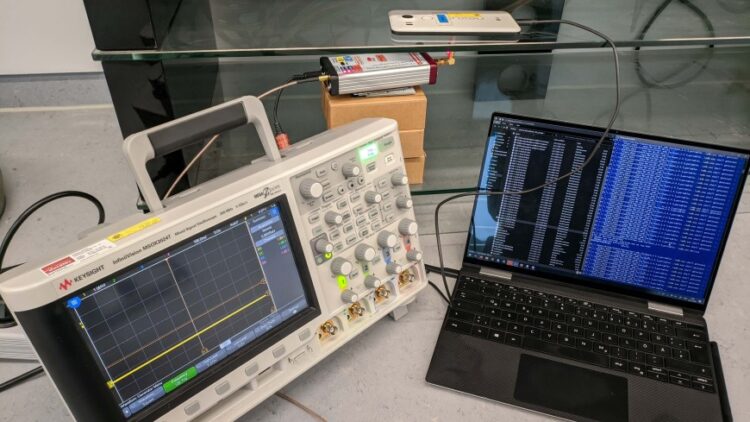
GhostTouch attack scenario in the lab: The attacker uses an EMI device under a table to attack the touchscreen of a smartphone that is lying on the table with the display facing down.
Picture: Richard Mitev
International research project confirms possibility for attacks on touchscreens.
Usually, an action by the user, such as accidentally clicking on a link, is required to install malware on a smartphone. However, scientists at TU Darmstadt and Zhejiang University have now succeeded in remotely controlling smartphones by imitating touches on the touchscreen.
In an international research project, scientists at the System Security Lab of TU Darmstadt and Zhejiang University in Hangzhou managed, for the first time, to perform targeted attacks on capacitive touchscreens. Using the so-called “GhostTouch”, the researchers were able to use electromagnetic interference (EMI) to simulate touches on the display and thus remotely control the smartphone. In three different attack scenarios, nine out of twelve smartphone models tested could be manipulated.
To realize the attack, the research team had to solve two main technical challenges: First, the difficulty of affecting the touchscreen at all through electromagnetic interference, and second, creating predictable and controllable touches. “In our attacks, we varied the power of the EMI transmitting antenna, the signal frequency, and the distance from the phone display to trigger touches such as taps or swipes with the appropriate signal strength,” explains Richard Mitev, a PhD student at the System Security Lab.
Realized attacks on touchscreens
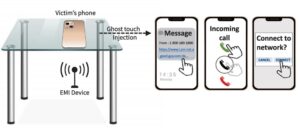
Using fake touches, the attacker can trick the smartphone into (1) clicking on a link that contains malware, (2) connecting to a malicious network, and (3) launching an eavesdropping attack on a phone call.
Picture: Richard Mitev
In order to achieve simultaneous controlled touches, the scientists examined the screens of the tested smartphone models in detail in advance. Each device model is based on specific movement patterns for actions such as unlocking, selecting or scrolling. By precisely tuning the parameters of the electromagnetic signal, it was possible to simulate these movement patterns with specifically positioned touches.
Using the “GhostTouch” and the touches it faked, the following threats could be turned into reality in practical attack scenarios, such as the injection of malware: If attackers knows the phone number of the victim, they can send a message containing a malicious link, for example. If the phone displays a notification for the received message, the attacker can open the notification using the “GhostTouch” and click on the link to download, for example, the malware that is embedded in the link.
In addition, the attacker can establish a sneaky connection via WiFi or Bluetooth. For example, he can control the phone with a Bluetooth mouse or perform a man-in-the-middle attack, which can be used to capture communications. In the third scenario, the attacker accepts a call via “GhostTouch” so that an eavesdropping attack can be launched and the victim can be bugged.
Take care, modern touchscreens are vulnerable
Although modern screens are subjected to careful electromagnetic tests and feature a protective anti-interference design, it was possible to generate targeted, contactless touches on nine of the twelve smartphone models tested and thus implement attacks. This demonstrates that the functionality of even the most modern touchscreens can be manipulated under certain conditions using the right equipment, and that they should not be blindly trusted.
The research results will be presented at this year’s USENIX Security Conference between August 10 and 12 in Boston.
About TU Darmstadt:
TU Darmstadt is one of Germany’s leading technical universities and a synonym for excellent, relevant research. We are crucially shaping global transformations – from the energy transition via Industry 4.0 to artificial intelligence – with outstanding insights and forward-looking study opportunities. TU Darmstadt pools its cutting-edge research in three fields: Energy and Environment, Information and Intelligence, Matter and Materials. Our problem-based interdisciplinarity as well as our productive interaction with society, business and politics generate progress towards sustainable development worldwide. Since we were founded in 1877, we have been one of Germany’s most international universities; as a European technical university, we are developing a trans-European campus in the network, Unite! With our partners in the alliance of Rhine-Main universities – Goethe University Frankfurt and Johannes Gutenberg University Mainz – we further the development of the metropolitan region Frankfurt-Rhine-Main as a globally attractive science location.
MI-Nr. 08e/2022, Fröhlich/sip
Wissenschaftliche Ansprechpartner:
Prof. Ahmad-Reza Sadeghi,
Head of System Security Lab, TU Darmstadt
E-Mail: ahmad.sadeghi@trust.tu-darmstadt.de
Originalpublikation:
https://www.usenix.org/system/files/sec22summer_wang-kai.pdf
https://www.tu-darmstadt.de/universitaet/aktuelles_meldungen/einzelansicht_352192.en.jsp
Media Contact
All latest news from the category: Information Technology
Here you can find a summary of innovations in the fields of information and data processing and up-to-date developments on IT equipment and hardware.
This area covers topics such as IT services, IT architectures, IT management and telecommunications.
Newest articles

Innovative 3D printed scaffolds offer new hope for bone healing
Researchers at the Institute for Bioengineering of Catalonia have developed novel 3D printed PLA-CaP scaffolds that promote blood vessel formation, ensuring better healing and regeneration of bone tissue. Bone is…

The surprising role of gut infection in Alzheimer’s disease
ASU- and Banner Alzheimer’s Institute-led study implicates link between a common virus and the disease, which travels from the gut to the brain and may be a target for antiviral…

Molecular gardening: New enzymes discovered for protein modification pruning
How deubiquitinases USP53 and USP54 cleave long polyubiquitin chains and how the former is linked to liver disease in children. Deubiquitinases (DUBs) are enzymes used by cells to trim protein…



